August 2011 IT Business Consulting Newsletter
Virtual Private Networks (VPNs) – a key Business Enabler
By Tom K
You have staff wanting to work from home, traveling staff who need to access company resources, and managers that need access to business resources from wherever, whenever.
Or you need to transparently connect that new remote office to your main office resources within a tight budget.
Enter the Virtual Private Network, or VPN. These gems allow you to connect remote offices securely and inexpensively, and enable your staff to work remotely from anywhere.
In this month’s newsletter I’ll explain what VPNs are, how to deploy them, and how you can use them to improve your business performance at little cost.
The VPN – What is it?
In simple terms, think of a VPN as a very long Ethernet cable running from the back of the remote user’s Laptop through the Internet, and plugged into the wall inside your office. A properly designed VPN provides the remote worker secure access to all the network resources they can access form their office PC.
More technically, the VPN is a tool that enables passing data securely through a public network (the Internet). Normally, data passing over a public network is not secure. The VPN uses a combination of hardware and software to build an encrypted data tunnel through the public network. This tunnel creates a “virtual private network” within the public network, providing secure data transmission.
Two Different Connectivity Uses - Remote Users & Remote Offices
The Remote User is a pretty simple concept. As above, the mythical super-long Ethernet cable gives the remote user secure access to all the network resources she can access from her office PC, from anywhere in the world... home office, hotel at VRMA, poolside in the Bahamas, etc.
The Remote User VPN includes an authentication structure so that when someone connects to your private network via a VPN they are authenticated and given access to your network. Once on the network (the super-long cable is plugged in) the user must log into your network to receive selected access to company resources based on their identity.
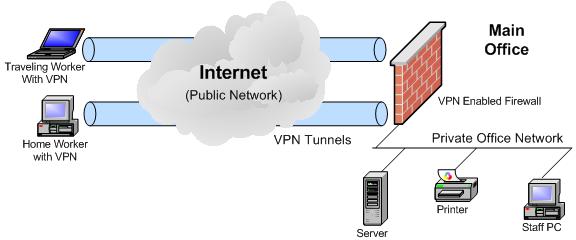
The Remote Office is equally simple. Rather than purchasing relatively expensive dedicated comm circuits from the data carriers, use your inexpensive office Internet circuits and an “always on” Site-to-Site VPN to provide inexpensive, secure connectivity between your offices. This VPN is always up, and is transparent to the users. Remote Office users log on to the network when their PCs boot up to receive access to their assigned company resources, just like the users at the main office.
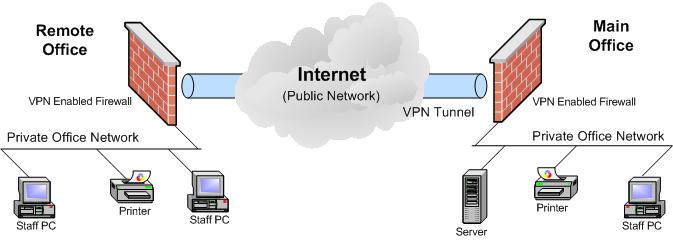
Comm circuits cost from several hundred to several thousand dollars per month depending on the circuit type and bandwidth. Internet circuits typically cost one to two hundred dollars per month. While dedicated comm circuits do tend to be somewhat more reliable than standard Internet circuits, it is quite easy to load balance two Internet circuits at each office for full redundancy at a fraction of the cost of dedicated comm circuits (see our April 2009 Newsletter: Improving the Reliability & Speed of Your Business Internet Connection).
Using Firewalls to Deploy VPNs
On Wall Street, we used rather expensive “VPN Appliances” that provided 100’s of concurrent VPNs (100’s of remote staff could connect to the private network simultaneously). Most Property Managers’ VPN needs are much simpler, and can be provided essentially for free using Firewalls.
Your business networks should always connect to the Internet through Firewalls... If they do not, we really need to talk!
Most Firewalls being marketed today have VPN capabilities built in, some as part of the core product, some as an extra cost add-on key. If you only deploy Remote User VPNs, you’d need one VPN enabled Firewall at your main office. If you are connecting remote offices via VPNs, you’d need an additional VPN enabled Firewall at each remote office. But, as mentioned above, you really should have a Firewall protecting every office that is connected to the Internet.
Firewalls are usually licensed for the number of concurrent VPNs allowed. For instance, the Firewall we most often use at the main office allows 50 concurrent IPSec VPNs and 5 concurrent SSL VPNs, at a cost of about $375. The Firewall we use at remote offices allows 2 IPSec VPNs for about $130.
Two Prevalent VPN Types - IPSec and SSL
In "the old days” there was only the IPSec VPN. It is still very much in use today, but the new kid on the block is the SSL VPN.
The IPSec VPN requires a small piece of software on the remote user’s PC which is used to set up the VPN with your main office Firewall. The software is relatively inexpensive ($50 - $150 depending on feature set), and is easily configured. As noted above, most Firewalls support many more concurrent IPSec VPNs than SSL VPNs, so we still use IPSec VPNs a lot.
We also use IPSec VPNs for Remote Office VPNs, as they are easy to set up on the two Firewalls, require no additional software, and a single remote office IPSec VPN will support all the users in the remote office simultaneously.
The SSL VPN is pretty cool in that it requires no software on the remote user’s PC. The remote user connects using any Internet Browser, enters her credentials at the prompt, is authenticated by the Firewall, and is connected. Once the Firewall has been configured for SSL VPN, connectivity is very easy for the user to use.
How to Use VPNs
Remote User IPSec VPNs - the user launches the VPN software, which connects the VPN to the main site Firewall. The VPN authentication is automatic, as the “keys” are in the software configuration.
Remote User SSL VPNs - the user launches any Internet Browser and points it to the Firewall. They need to enter their user ID and password into the log-on screen & then their VPN is connected.
In either case, once the VPN is connected, the user needs to authenticate to the network to access network resources.
Site-to-Site IPSec VPNs - the user needs only to log into the network when they log on to their PC. The remote site is always connected to the main site via the VPN, and the remote users interact with the main site network as if they were sitting in the main office.
A Business Enabler
Imagine the advantages of key personnel being able to work from home when the kids are sick, managers having instant access to data necessary to assess and resolve problems while out of town, and the business owner being able to check the financials when she gets that brainstorm at 1 AM. These are but some of the obvious benefits.
Think outside the lines... Consider an IP phone system working with the VPN. Your reservation staff can work from anywhere, with only a laptop, a soft phone, and a headset. With the VPN they’d have full access to the data system and be signed into the reservation phone queue.
If you have any questions concerning implementing VPNs (or any other topics concerning utilizing your infrastructure to enhance your business), I’d be happy to discuss them with you at your convenience. Feel free to contact me at TomK@TomKConsulting.com, or via my cell 443.310.5110.
Next month I’ll discuss the concerns IT should have relating to departing employees, the steps we recommend to properly deal with security and auditing, and different processes used when the departing employee is leaving with blessings or in handcuffs. See "Departing Employee? How to Process them Gracefully and Securely".